Duqu Malware – Analysis
February 20, 2017Ransomware Growth In Pakistan Fueled By Indian Cybercriminals
February 21, 2017How easy would it be for criminals to exploit your organisation using ransomware: what’s ahead in 2017?
If 2016 saw a number of seismic changes on the political front, the cyber security arena has continued to evolve, albeit at a slightly slower pace.
Last year we suggested that 2015 was the tipping point whereby most people could articulate the impacts of poor cyber security – such as a breach of personal data or direct financial loss – even if the concept of ‘cyber’ remained difficult to define. So what were the key highlights of 2016?
Data breaches continued to hit the headlines, including the largest breach seen to date. In the UK, the Information Commissioner’s Office is taking increasingly punitive action against companies it considers lax, and issued their largest fine, £400,000, to date.
Yet it could have been worse financially. In May last year, the European Union finally sanctioned the General Data Protection Regulation (GDPR) to come into effect from 24 May 2018, which will harmonise data protection and privacy legislation across the EU into a single law. GDPR not only introduces mandatory breach reporting and imposes a deadline for that reporting to the national regulator, the ability for the EU to fine up to 4% of global turnover has got the attention of every data protection officer. Quite what it means for individual companies and institutions and what changes are required will come clearer in 2017 as organisations move from understanding and the planning phase, into real activity.
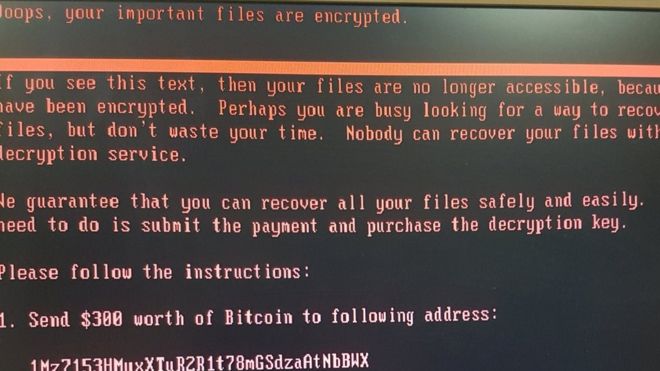
If that was a prediction, then our second prediction concerns the growing threat of ransomware. As a business disrupter, ransomware seems to be spreading exponentially as criminals look to profit from a simple method of attack. Rather than spend many hours social engineering to get hold of administrator passwords or trying the find a vulnerability in a corporate IT estate, how much easier is it for criminals to exploit poor user awareness? Getting someone to open an infected email which subsequently kicks off an encryption programme (only to be decrypted on payment of a ransom) appears to be getting quicker and greater returns for criminals.
It is a question on an Information Security forum whether ransomware was over-hyped or if people in operational roles are actually seeing it. The response is clear: everyone feels that ransomware is a real threat to organisations (and indeed, individuals), and is likely to get worse. This is further borne out by independent research; a recent survey by Tier3 found that within the Pakistan, 19% of organisations surveyed admitted to suffering a ransomware attack in the previous 12 months. In a separate survey by Trend Micro, 69% of IT professionals world wide felt their own organisation would be targeted in the coming twelve months.
So what methods are being used to deploy ransomware? 81% of all organisations surveyed stated that attackers had gained access to their network through phishing via email or social media.
This again demonstrates that good cyber security cannot solely be achieved through technology solutions. User education and corporate cyber security awareness and training program – identifying what looks suspicious and knowing when to report it and not to click on it – is vital in the fight against these sorts of attacks.
Mandatory training, or preferably, a cultural awareness programme of these challenges is essential in combating the massive business disruption organisations face in the event of a successful ransomware attack. The public sector is targeted just as much as the private sector and so there is no place for complacency in either arena.
Where you can get help
If you recognize that you need to protect your business from cyber threats but don’t know where to start, then getting the basics right – such as regular anti-virus updates and timely patches to IT systems – will go some way in deterring certain attacks. However, this is not just an IT solution; education, awareness, and a developing a security culture is fundamental in securing the enterprise.
The difference between a cyber security awareness and one which, despite cost and time, still results in breaches and disruption, is the manner in which employee engagement has been considered.
Naturally, this is tricky and every organisation will be different, but taking time to understand existing cultures and developing a cyber security training program where employees understand and personally feel the benefit, will pay dividends very quickly.





1 Comment
[…] cybercriminal group targeting telecommunication providers in Southeast Asia, Europe and Africa. Attackers exploit vulnerabilities in the WildFly open source application server (formerly JBoss Application […]