Tier3 provides Pentesting and technical consultation services for Payment Card Industry Data Security Standard – PCI DSS Compliance in Pakistan. Our PCI Pentesting service satisfy conditions as set by PCI DSS v4.0 11.4. Driven by the increasing requirements for cyber risk assessments, we know the demand for pentesting services is at an all-time high.
Our Pentesting service for PCI DSS compliance is delivered by certified pentesters who do tailored and manual pentesting for compliance framework to uncover complex logic errors and unknown vulnerabilities. Our pentesters deliver the specific report you need – to satisfy compliance requirements.
PCI DSS Pentesting in Pakistan
PCI DSS Penetration Testing
Tier3 certified professionals deliver pentesting services tailored for the Payment Card Industry Data Security Standard (PCI DSS) v4.0 to help you meet its requirements efficiently. We will help you determine the scope of your cardholder data environment (CDE) to be tested from an internal and external perspective. We deliver a thorough Penetration Test Report and an accompanying Fix Action report that can be shared with your auditor of choice.
Our Fix Action report and the monitoring platform will provide the actionable insights your organization will need to remediate your system vulnerabilities. We will also provide a detailed remediation guidance for addressing weaknesses efficiently at a systemic level as well as individually.
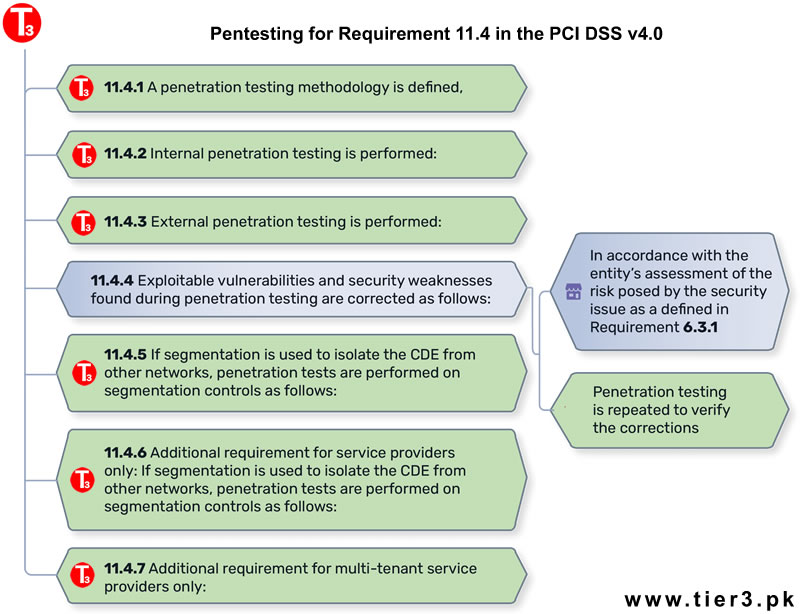
Pentesting for Requirement 11.4 in the PCI DSS v4.0.
Our custom specifically built pentesting management platform with ability to independently verify remediations and fixes saves your team valuable time and also ensures readiness if the penetration test has to be repeated to fulfill (PCI DSS Ver 4.0 Section 11.4.4).
All PCI pentesting results and remediation activities conducted via our platform are securely stored for 12 months, adhering to PCI DSS requirement (PCI DSS Ver 4.0 Section 11.4.1).
PCI-DSS applies to all companies that store, process, or transmit cardholder data, whereas PA-DSS applies to vendors that produce and sell payment applications. Our experts can take your team through whole process and can help in achieving benchmarks as required by the standards organisation.

PCI DSS Compliance in Pakistan
The Payment Card Industry Data Security Standard (PCI DSS) applies to companies of any size that accept credit card payments. If your company intends to accept card payment, and store, process and transmit cardholder data, you need to host your data securely with a PCI compliant hosting provider.
Tier3 also helps and consults Mobile Apps or software developers to achieve PA-DSS (Payment Application Data Security Standard) compliance standard specifically for software vendors that develop point-of-sale (POS) and other mobile applications to accept credit card payments.
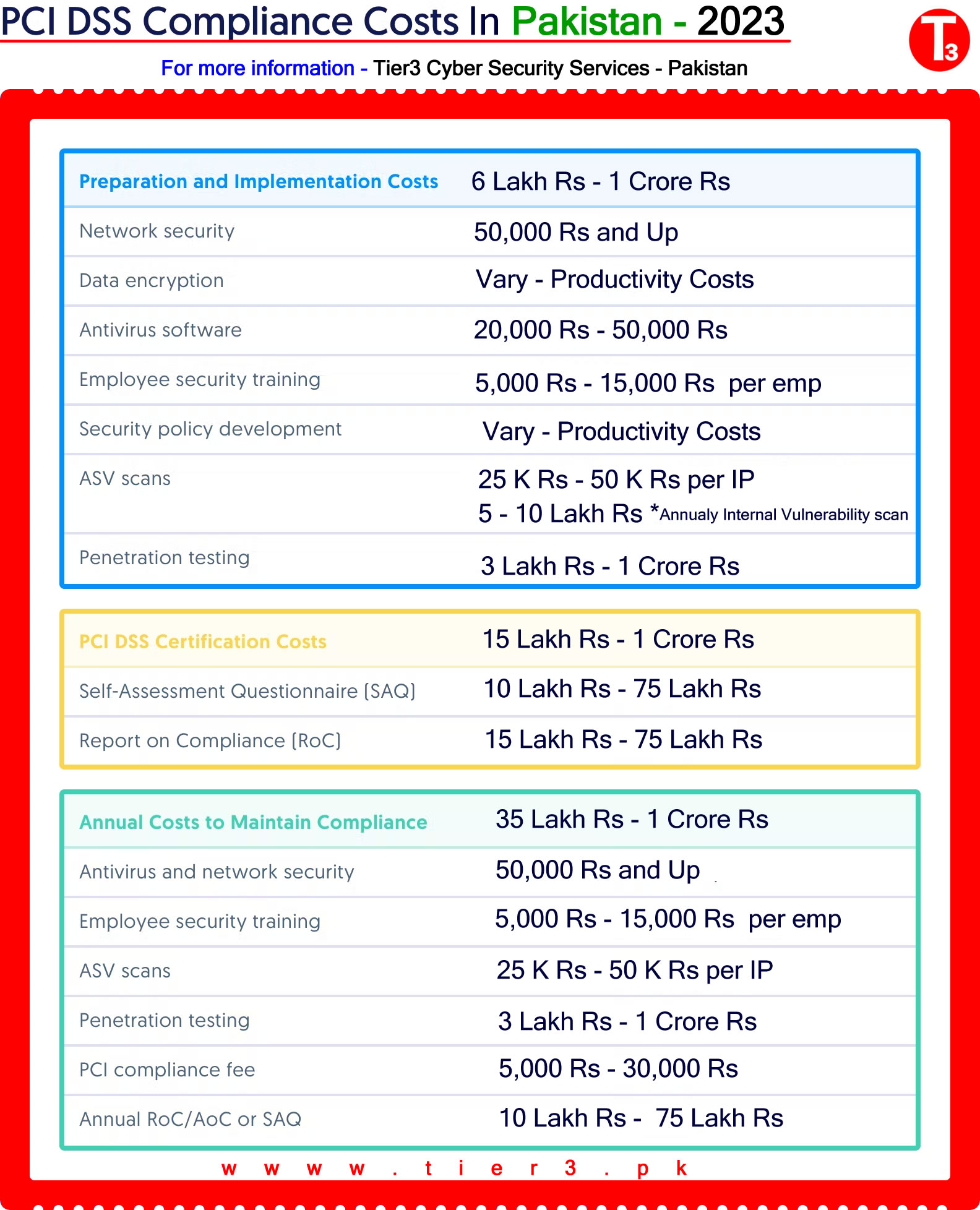
PCI DSS Cost in Pakistan
PCI DSS isn’t a one-size-fits-all framework. The level of compliance you need is based on factors like:
- The size and business type of your organization
- The number of transactions you process each year
- The requirements of your customers and acquiring bank or merchant
So PCI DSS compliance costs vary quite a bit based on these same factors. A global or national enterprise that processes millions of credit card transactions a year is going to be looking at a much higher compliance bill than a small e-commerce shop. Your level of PCI DSS readiness is another big factor influencing PCI costs. The more work you need to do to bring your policies, processes, and system configurations up to par, the more expensive your total certification costs will be.
That said, every organization that pursues certification will likely incur some of the same costs, but based on preparedness it may be beneficial for a company to undergo a full readiness assessment versus needing only some consulting hours.
Below, we list some typical costs of preparing for, achieving, and maintaining PCI compliance.
PCI DSS Costs in Pakistan
Like vulnerability scans, penetration tests help you find vulnerabilities in your cardholder data environment before they can be exploited by an actual attacker. Penetration tests are required to be performed manually and segmentation testing is required to be performed every 6 months for service providers. Penetration testers (also known as ethical hackers) specifically look for security issues that automated scanning systems may not identify and will exploit vulnerabilities found to verify the extent of the security issues within your environment.
Penetration tests are required annually for PCI RoC, SAQ D, SAQ C, SAQ C-VT, SAQ B-IP, and SAQ A-EP.
PCI DSS Annual audit costs
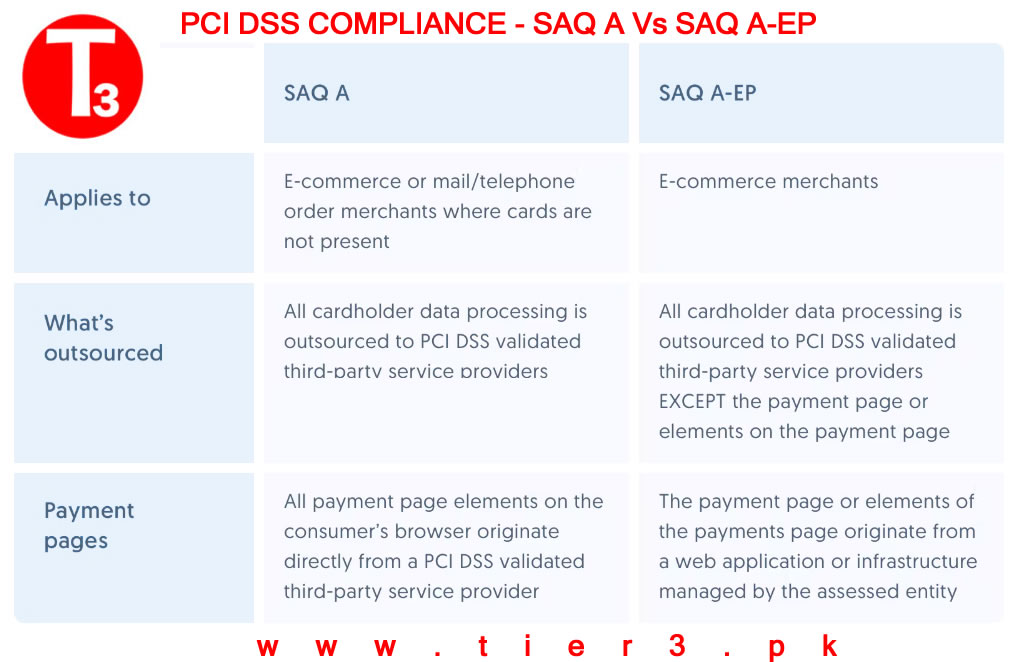
Once you’ve fully prepared for PCI DSS certification, you’re ready for either a Self-Assessment Questionnaire or Report on Compliance. Because certification lasts one year, plan for these certification costs to be an annual recurring investment. A Self-Assessment Questionnaire (SAQ) is a document that asks questions step-by-step through each PCI requirement and allows you to determine your level of compliance based on your implementation and if the implementation meets the requirements. Unless you’re a Level 1 merchant or service provider, your organization qualifies for an SAQ. We recommend using an auditor to help qualify your SAQ and perform the assessment on your behalf to ensure the SAQ will pass any requirements from your customers or acquiring banks.
Level 1 merchants and service providers — as defined by the PCI SSC or based on your customer requirements —are required to complete a Report on Compliance (RoC). All other organizations would need to complete a Self-Assessment Questionnaire (SAQ).
Level 1 merchants and service providers are required to undergo a full report on compliance audit. At the end of your audit, the QSA will issue a Report on Compliance (RoC) and Attestation of Compliance (AoC) that details your organization’s cardholder data environment, security posture, and level of PCI DSS compliance.
Your RoC/AoC or SAQ is valid for one year, so you’ll need to complete the process annually to maintain certification. The cost of your SAQ documentation and/or security audit is something you’ll incur every year.
PCI DSS SQA-A Pakistan
The 12 requirements of PCI DSS
- Install and maintain a firewall configuration to protect cardholder data
- Do not use vendor-supplied defaults for system passwords and other security parameters
- Protect stored cardholder data
- Encrypt transmission of cardholder data across open, public networks
- Use and regularly update anti-virus software or programs
- Develop and maintain secure systems and applications
- Restrict access to cardholder data by business need to know
- Assign a unique ID to each person with computer access
- Restrict physical access to cardholder data
- Track and monitor all access to network resources and cardholder data
- Regularly test security systems and processes
- Maintain a policy that addresses information security for all personnel
Goal: Building and maintaining a secure network.
Install and maintain a firewall configuration to protect cardholder data. Companies must create their own firewall configuration policy and develop a configuration test procedure designed to protect cardholder data. Your hosting provider should have firewalls in place to protect and create a secure, private network. Do not use vendor-supplied defaults for system passwords and other security parameters. This means creating, maintaining and updating your system passwords with unique and secure passwords created by your company, not ones that a software vendor might already have in place when purchased.
Goal: Protect Cardholder Data.
Protect stored data.This requirement only applies to companies that store cardholder data. Specifically, companies that do not automatically store cardholder data are already avoiding a possible data security breach often targeted by identity theft.
A PCI compliant hosting provider should provide multiple layers of defense and a secure data protection model that combines physical and virtual security methods. Virtual security includes authorization, authentication, passwords, etc. Physical includes restricted access and server, storage and networking cabinet locks and other aspects of Physical Security.
Encrypt transmission of cardholder data across open, public networks. Encrypted data is unreadable and unusable to a system intruder without the property cryptographic keys, according the PCI Security Standards Council. Cryptographic keys refers to the process in which plaintext, like the words seen here, are transformed into ciphertext. Ciphertext contains information unreadable to those without the cipher, or the specific algorithm that can decode the text.
As an added security measure, sensitive authentication data, including card validation codes or PIN numbers, must never be stored after authorization – even if this data is encrypted.
Goal: Maintain a Vulnerability Management Program.
Use and regularly update anti-virus software. An anti-virus software service needs to be frequently updated to protect against the most recently developed malware. If your data is being hosted on outsourced servers, a managed server provider is responsible for maintaining a safe environment, including generating audit logs.
Develop and maintain secure systems and applications. This includes discovering newly identified security vulnerabilities via alert systems. Your PCI compliant hosting provider should be monitoring and updating their systems to accommodate any security vulnerabilities.
Goal: Implement Strong Access Control Measures
Restrict access to cardholder data by business need-to-know. Limiting the number of personnel that have access to cardholder data will lessen the chances of a security breach.Assign a unique ID to each person with computer access. User accounts with access should follow best practices, including password encryption, authorization, authentication, password updates every 30 days, log-in time limits, etc.
Restrict physical access to cardholder data. If your data is hosted in an off-site data center, your data center provider should have limited personnel with access to the sensitive information. PCI compliant data centers should have full monitoring, including surveillance cameras and entry authentication to ensure a secure and PCI compliant hosting environment.
Goal: Implement Strong Access Control Measures
Track and monitor all access to network resources and cardholder data. Logging systems that track user activity and stored archives can help your hosting provider pinpoint the cause in the event of a security breach or other issue. Regularly test security systems and processes. With regular monitoring and testing processes in place, your data hosting provider should be able to assure you that your customers’ cardholder data is safe at all times.
Goal: Maintain an Information Security Policy
Maintain a policy that addresses information security. This policy should include all acceptable uses of technology, reviews and annual processes for risk analysis, operational security procedures, and other general administrative tasks.
Payment Application Data Security Standard (PA DSS)
The Payment Application Data Security Standard (PA-DSS), formerly referred to as the Payment Application Best Practices (PABP), is the global security standard. Payment Application Data Security Standard (PA-DSS) is a set of requirements intended to help software vendors develop secure payment applications for credit card transactions. This ensures that companies do not store prohibited data, such as the security PIN, magnetic strip or CVV2. The PA-DSS applies to software vendors and others who develop software systems or mobile application that support payment applications that store, process, or transmit cardholder data and/or sensitive authentication data.
Payment applications that are sold, distributed, or licensed to third parties are subject to the PA-DSS requirements. For a payment application to be deemed PA-DSS compliant, software vendors must ensure that their software includes the following fourteen protections:
- Do not retain full track data, card verification code or value (CAV2, CID, CVC2, CVV2), or PIN block data.
- Protect stored cardholder data.
- Provide secure authentication features.
- Log payment application activity.
- Develop secure payment applications.
- Protect wireless transmissions.
- Test payment applications to address vulnerabilities and maintain payment application updates.
- Facilitate secure network implementation.
- Cardholder data must never be stored on a server connected to the Internet.
- Facilitate secure remote access to payment application.
- Encrypt sensitive traffic over public networks.
- Secure all non-console administrative access.
- Maintain a PA-DSS Implementation Guide for customers, resellers, and integrators.
- Assign PA-DSS responsibilities for personnel, and maintain training programs for personnel, customers, resellers, and integrators.
Tier3 is leading cyber security service providers in Pakistan. Our team can help your business to get its PCI DSS compliance, PCI DSS Penetration Testing or PA-DSS Compliance with PCI Security Council. Please contact us today for more information.


