Manipulation and Interference of Information in Pakistan – Cyber Security Guide
October 20, 2023
Best Practices for Safeguarding Software Supply Chains: Adopting Software Bill of Materials
November 11, 2023Tier3 Pakistan and its partners are responding to active, widespread exploitation of two vulnerabilities, CVE-2023-20198 and CVE-2023-20273, affecting Cisco’s Internetworking Operating System (IOS) XE Software Web User Interface (UI). Cisco’s IOS XE Web UI is a system management tool for IOS XE, which is a network operating system for use on various Cisco products. An unauthenticated remote actor could exploit these vulnerabilities to take control of an affected system. Specifically, these vulnerabilities allow the actor to create a privileged account that provides complete control over the device.
Tier3 Threat intelligence team has found more than 600 systems using Cisco’s IOS XE Web UI in Pakistan. (Shodan dork for CVE-2023-20198: “http.html_hash:1076109428 “)
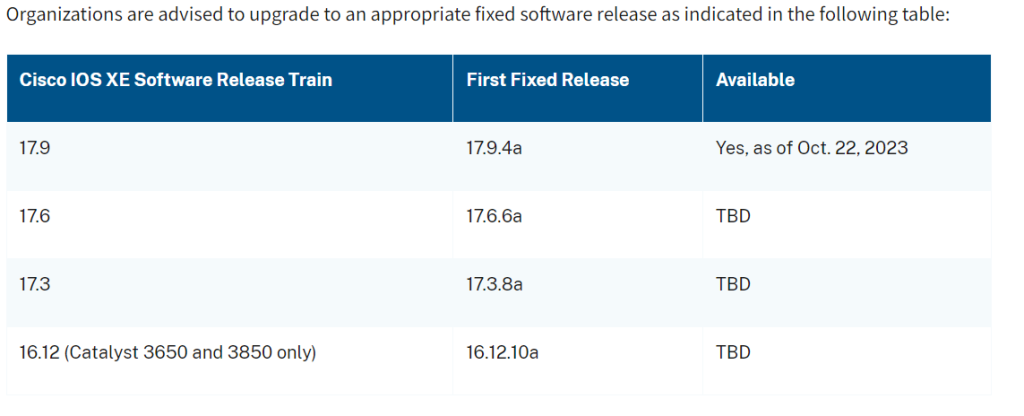
Organizations running IOS XE Web UI should immediately implement the mitigations outlined in Cisco’s Security Advisory, Multiple Vulnerabilities in Cisco IOS XE Software Web UI Feature, which include disabling the HTTP Server feature on internet-facing systems and hunt for malicious activity on their network. Organizations should also look for unexplained or newly created users on devices as evidence of potentially malicious activity relating to this threat.
Technical Details of Vulnerability
CVE-2023-20198 is a privilege escalation vulnerability in the web UI feature of Cisco’s IOS XE software affecting both physical and virtual devices that have the HTTP or HTTPS Server feature enabled. Exploitation of this vulnerability allows an actor to gain full administrative privileges and unauthorized access into affected systems. After obtaining the privileged account, the actor can then create a local user account with normal privileges to exploit another IOS XE Web UI vulnerability, CVE-2023-20273, to inject commands with elevated (root) privileges, enabling the actor to run arbitrary commands on the device.
According to the Cisco Talos blog referenced above, a threat actor can:
- Exploit CVE-2023-20198 to obtain initial access and create a privileged account.
- Use the privileged account to create a local user account with normal privileges.
- Using the local user account, exploit another Cisco IOS XE Web UI vulnerability—CVE-2023-20273—to inject commands with elevated (root) privileges, which enables the actor to run arbitrary commands on the device.





