
Mitigating Cisco IOS XE Web UI Vulnerabilities – CVE-2023-20198 and CVE-2023-20273
October 24, 2023
Secure AI system development
November 30, 2023Cyberattacks in the digital realm aim to disrupt or compromise computing environments, exemplified by incidents like SolarWinds and Log4j exploits. These incidents underscore vulnerabilities in software supply chains affecting both commercial and open source software, impacting private and government enterprises. The growing threat calls for heightened awareness and vigilance in securing software supply chains, recognizing the potential weaponization by nation-state adversaries using similar tactics.
Addressing these concerns is crucial for organizations to fortify their defenses against evolving cyber threats. In the realm of software supply chains, vendors play a pivotal role as intermediaries between customers and developers. This entails upholding software integrity and security through contractual commitments, timely releases, notifications, and vulnerability mitigation. Here we try to outline industry’s best practices, emphasizing the management of open source software and software bills of materials. It serves as a valuable resource for both software developers and suppliers, offering guidance aligned with security principles and fostering awareness about software security.
The common threats to software supply chains are design flaws, vulnerable third-party components, network infiltrations, and malicious software injection. Public and private sector stakeholders must prioritize ongoing security measures, tailoring efforts to their specific domains. Collaboration and shared responsibility among stakeholders are essential for effective mitigation in this dynamic cybersecurity landscape.
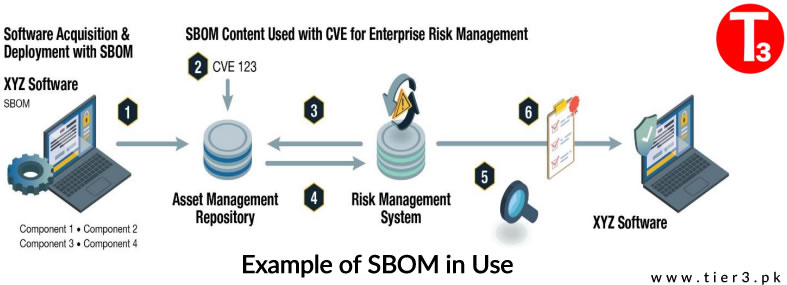
A Software Bill of Materials (SBOM) is a key building block in software security and software supply chain risk management. An SBOM is an inventory, a list of ingredients that make up software components used by organization. SBOM has two widely used machine-readable formats: Software Package Data Exchange (SPDX) and CycloneDX. SBOMs provide improved visibility into the pedigree of the software that the customer organization is evaluating, deploying, and/or operating within their environment. This increased visibility into all software is critical for proper supply chain risk management and overall enterprise risk management.
Software consumers benefit from a quality Software Bill of Materials (SBOM), providing confidence in a supplier’s ability to address supply chain concerns. Leveraging SBOM for cyber security threat intelligence enhances software security, ensuring updates and patches against known vulnerabilities, fostering a robust defense mechanism for users. For example, licensing information derived from SBOMs can help businesses ensure that they comply with licensing requirements when using open source or 3rd party licensed software.
The Software Bill of Materials (SBOM) enhances transparency, empowering organizations with improved software asset, patch, and vulnerability management. As the primary purpose of an SBOM is to identify components and their relationships to one another, hence it also offers valuable supply chain risk data insights.
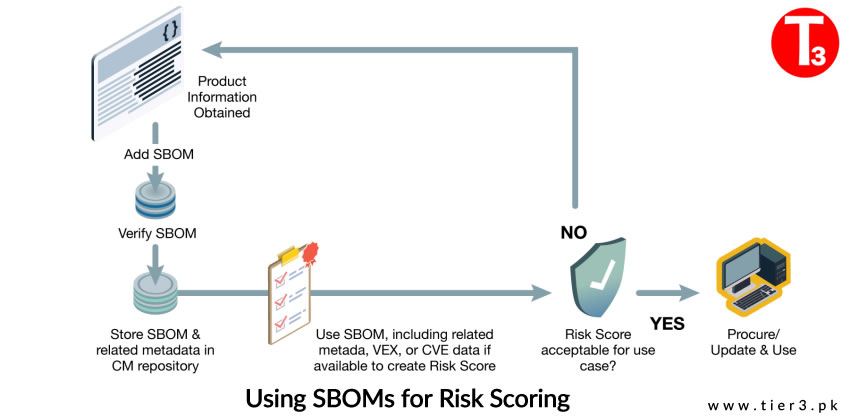
A customer may request or receive SBOMs in various ways through a variety of mechanisms:
• As part of contractual procurement of a commercial product
• As part of or alongside the download of commercial closed-source software
• As part of a contractual procurement of professional services that includes the development and delivery of software capabilities
• As part the acquisition of open-source software applications or components
• During the discovery processes as a device connects to a network
• Delivered directly to the customer via the supplier/developer
• Through a customer portal or some other pre-arranged mechanism
• Through a service or repository designed to help deliver software metadata.
Once an SBOMs is processed, SBOM information can be provided to the variety of SBOM information consumers within the customer enterprise:
- Configuration management databases (CMDBs)
- Software asset management (SAM) systems
- Security operations centers (SOCs)
- Procurement workflows, which may include pre-procurement diligence, contractor/vendor
management systems, and third-party risk and compliance management and reporting - Software supply chain risk assessment and management functions
Software Bill of Materials (SBOM) consumption is an evolving practice expected to scale with the aid of emerging tools designed for automation. Various organizations will prioritize different risks, leveraging software transparency for better management. As the industry envisions more use cases for SBOM, its increasing prevalence is anticipated. Despite ongoing developments, simply requesting and maintaining SBOMs holds value, especially for swift response to emergency advisories. It’s crucial to recognize that SBOM is just one facet of software supply chain security; adhering to basic hygiene and heeding other Cyber Supply Chain Risk Management (C-SCRM) guidance remains imperative.





