Authorities Issue Alert Warning of Potential for Cyber Attacks
February 18, 2019
WhatsApp Hacked – Vulnerable App used for Surveillance
May 14, 2019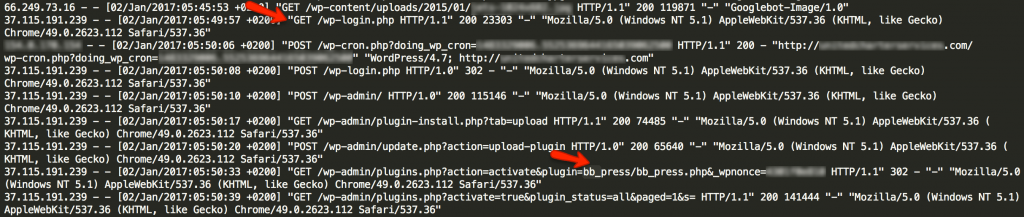
Fileless malware attacks are increasing every day.They can nowadays be seen as the perfect crime of opportunity. The initial vector of these attack can be a seemingly innocuous business email with a link to an invoice or some other business document. However, hiding within link could be a page with JavaScript or Powershell that opens the door to a greater threat. That script could stay fully fileless as it runs behind the scenes, accessing PowerShell,WMI and other operating system classes and registry entries for making commands to the user’s machine. In a worse case, it might use user’s own credentials to seek out other places to access with the network or domain.
Given the necessity of speed for today’s business networks and the computers on them, this malicious form of attack needs only a few seconds to start the damage on first host and begin to propagate across the network. That damage could be inflicted in many ways to both IT infrastructure and business itself. Its results could be destroying for an organization whose data is now at risk of being removed, destroyed, or encrypted. Further complicating the problem, as the IT and security teams comb through their data to see how such an attack began, there’s simply no evidence to find.
It’s as if someone has evaded all the layers of security and stolen the crown jewels without leaving a trace.
While fileless attacks present a real danger to organizations, their risks can be mitigated. The first step in protecting your environment is education. #OPsec Teams need to view file-based and fileless malware as two completely different types of attacks. Simply applying file-based tools and expectations to fileless attacks is a losing strategy. There are five important distinctions between the two approaches
- Analyze fileless code using System-Heuristics method
- Identify,analyze and decode concealed,obfuscated and encoded code.
- Detecting fileless attacks in real-time hidden and concealed within network and web traffic with no impact on network and host performance.
- To analyse and decide if “code” will execute benign or malicious operations in real-time.
- Detecting threats in real time and forward thinking.
While fileless malware isn’t a net-new threat, the complexity and volume of these attacks and techniques, threat actors employ to attack an organization’s networks are evolving every day.
Organisations can stay safe by addressing the challenges above, security teams can lay the required groundwork against these malware attacks for lowering their risk in real time scenarios while setting the foundations of a strong security posture of their organisation for years to come.
In order to prepared for this growing threat of fileless malware, security teams must undergo a philosophical shift in thinking and approach, beginning with a comprehensive re-examination of recent past incidents that lacked a clear initial attack vector.
Asking a simple question “was this fileless?” should help them prioritize training and investments. Once teams have identified existing problems and begins the process of addressing those issues, root causes, or deficiencies, they can use their experience to fill those fileless malware detection gaps present in all Anti-viruses and other end-point softwares.





1 Comment
[…] Fileless Malware Attacks -The Growing threat to Pakistani Enterprises April 9, 2019 […]