
Malverposting – Use of Social media to propagate malicious software and security threats
May 19, 2023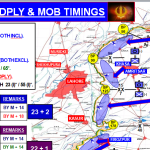
Hackers have released Indian Army battle plans for Pakistan
July 6, 2023A previously undocumented APT group tracked as GoldenJackal has been targeting government and diplomatic entities in the Middle East and South Asia since 2019. Kaspersky researchers have shared details about this activity, which has been ongoing since 2019. The primary motivation of this APT group appears to be the espionage.
The group focuses mainly on government and diplomatic entities in the Middle Easter and South Asian countries. Kaspersky started monitoring the operations of this group back in 2020, the researchers have explained that it showed a constant level of activity that demonstrates the capability of the group to fly under the radar.
The APT group uses a specific toolset of .NET malware, composed of JackalControl, JackalWorm, JackalSteal, JackalPerInfo and JackalScreenWatcher. The malware allows the group to:
- control their victim machines
- spread across systems using removable drives
- exfiltrate certain type of files from the infected system
- steal user credentials
- collect information about the local system and network
- collect information about users’ web activities
- screen captures of the victims’s desktop
Their malware uses HTTPS communications with the C2 servers, and supports the following operations:
- Execute an arbitrary program with provided arguments
- Download arbitrary files to the local file system
- Upload arbitrary files from the local file system
Researchers have observed that APT group updated their malware tools multiple times across the years.
In most of the attacks, the GoldenJackal APT used fake Skype installers and weaponized Word documents as initial attack vectors. The other known infection vector was a malicious document that uses the remote template injection technique to download a malicious HTML page, which exploits the Follina vulnerability.
Kaspersky researchers have observed a number of attacks against government and diplomatic entities in the Middle Eastern and South Asian countries including Afghanistan, Azerbaijan, Iran, Iraq, Pakistan and Turkey.
An advisory (Advisory Number 51 – 2022) was sent out by National Telecommunication and Information Technology Security Board (NTISB) back in 2022, about phishing activities related to this APT.





