
WhatsApp Hacked – Vulnerable App used for Surveillance
May 14, 2019
US – launched cyberattacks on Iran’s Systems
June 23, 2019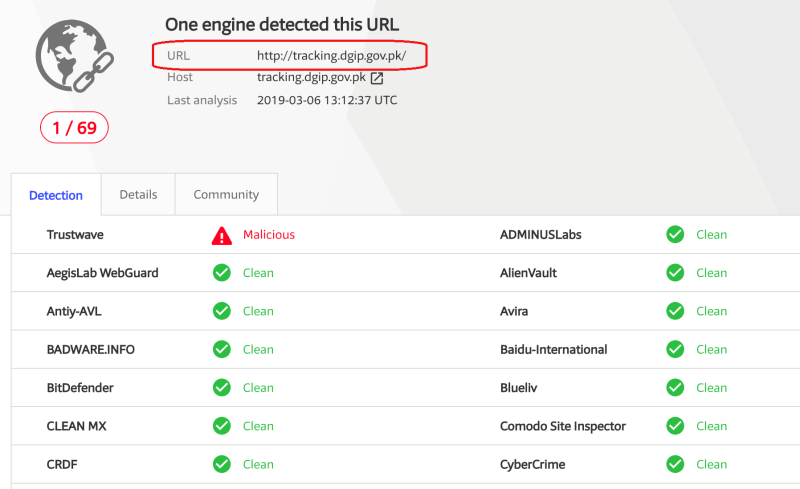
Scanbox framework used to hack Pakistani Govt’s passport application tracking site http://tracking.dgip.gov.pk
Experts uncovered a watering hole attack against the Pakistani Govt’s passport application tracking site, hackers used the Scanbox Framework to steal visitors’ data. Security experts at Trustwave have shared their findings of a recent data breach suffered by a Pakistani government website. The attackers used the Scanbox Framework, the intrusion is similar to another attack that last week hit the Bangladeshi Embassy in Cairo.
“Our earliest detection of Scanbox on this Pakistani government site was on March 2nd, 2019 and though we can’t say for sure how long before that Scanbox has been gathering information, we know with certainty that on that day alone Scanbox managed to collect information on at least 70 unique site visitors, about a third of them with recorded credentials.” reads the analysis published by Trustwave.
Attackers injected the Scanbox Javascript code to steal data about the visitors’ devices along with recording visitors’ keystrokes.
The application simply collects data from the host and send it to the command and control server, in particular, it is able to detect the applications running on the targeted machine and information that could be used later by an attacker to serve specific exploits.
Scanbox has numerous plugins that could be used to enumerates software installed in the system (e.g. Flash versions, Flash versions, etc.).The Scanbox framework is used by multiple APT groups, including the Stone Panda APT group and LuckyMouse, to carry out watering hole attacks.
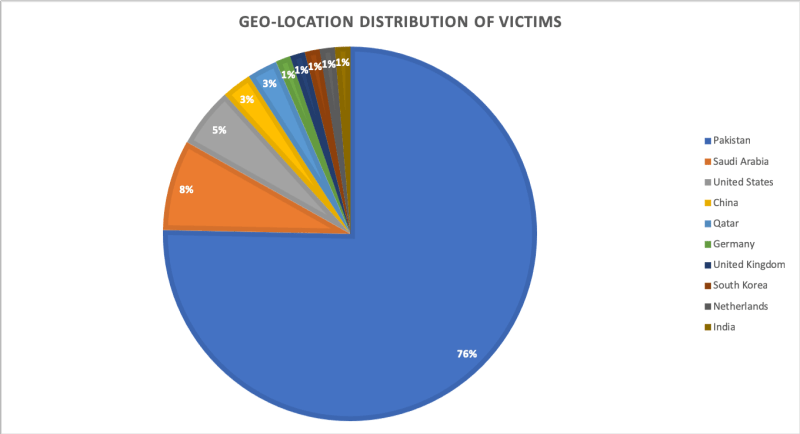
Most of the victims of the hack were, of course, Pakistani citizens, followed by Saudi Arabia, the United States, and China.Most of AV solutions were not able to detect the infection, Trustwave revealed that on the day it discovered the Scanbox infection, attackers obtained information about 70 unique visitors and login credentials of about one-third of them.
“These recent cases raise concerns regarding the security of government sites, especially ones where services provided online may involve access to sensitive information. From the perspective of an APT, a tool like Scanbox would only be the beginning of a potentially more elaborate attack.” concludes Trustwave.
This isn’t the first time that Pakistan entities are under attack, in November security firm Cylance uncovered a sophisticated state-sponsored campaign, tracked as Operation Shaheen, against the Pakistan Air Force.
In November, Group-IB experts a new large set of compromised payment cards details that was put on sale on Joker’s Stash, one of the most popular underground hubs of stolen card data. The new set of dumps, unauthorized digital copies of the information contained in magnetic stripe of a bank card, came with the payment details of 177,878 cards from Pakistani hackers and the other international banks.
In February, Group-IB experts discovered new databases with a total of 69,189 Pakistani banks’ cards that have shown up for sale on the dark web.
Source : https://securityaffairs.co/wordpress/82547/hacking/scanbox-pakistani-government-hack.html





1 Comment
[…] agencies had identified a major cyber attack by Indian intelligence agencies and APT groups. This cyber attack was targeting the mobile phones and personal gadgets of government officials and military […]