
Metasploit Pro In Pakistan
July 26, 2024
Fake Ransomware Rumors: The Truth About ATM Closures and Online Banking in Pakistan
August 21, 2024Cisco Password Management: Best Security Practices for Pakistan’s Cybersecurity Landscape
In today’s rapidly evolving digital world, the security of network infrastructure is a critical concern, especially in regions like Pakistan, where cybersecurity threats are on the rise. Cisco has also warned of multiple critical remote code execution zero-day vulnerabilities in Small Business SPA 300 and SPA 500 series IP phones widely used in Pakistan. Multiple vulnerabilities – tracked as CVE-2024-20450, CVE-2024-20452, and CVE-2024-20454 (CVSS score 9.8), in the web-based management interface of Cisco Small Business SPA300 Series IP Phones and Cisco Small Business SPA500 Series IP Phones could allow an attacker to execute arbitrary commands on the underlying operating system or cause a denial of service (DoS) condition.
Three years ago, Tier3 Cyber Security Pakistan issued a significant alert about cyber adversaries compromising network devices by obtaining hashed password values and other sensitive data from network configuration files. This incident highlights the risks associated with insecure, reversible password hashes and underscores the importance of robust password management practices.
The Growing Cybersecurity Challenge in Pakistan
Recent years have seen a worrying increase in the number of network infrastructure breaches, a trend that is particularly concerning for Pakistan’s burgeoning digital economy. Cyber adversaries exploit weak authentication protocols, poor password choices, and unencrypted transmission of router configuration files, making network devices vulnerable to attacks. In a region where cybersecurity infrastructure is still developing, these vulnerabilities can have far-reaching consequences.
The Importance of Strong Authentication Practices
For network administrators in Pakistan, the importance of securing authentication processes cannot be overstated. Network devices can be compromised through simple means such as:
- Weak passwords that fall prey to brute-force attacks
- Configuration files containing hashed passwords sent via unencrypted channels
- Reusing passwords across multiple devices, which can lead to widespread network compromise
While multi-factor authentication (MFA) is highly recommended, there are instances where only passwords are used. In such cases, selecting secure password storage algorithms becomes essential to safeguard against potential exploitation.
Cisco’s Role in Enhancing Network Security
Cisco® devices, widely used across many infrastructure networks, offer a range of password hashing and encryption schemes to secure stored passwords in configuration files. These devices are critical in directing network traffic and protecting sensitive data within subnets. However, the effectiveness of these security measures hinges on proper configuration.
Understanding Password Hashing and Encryption
- Hashing is a one-way algorithm that makes it difficult to reverse the output to the original string. Using a strong password with a random salt before hashing significantly reduces the risk of exploitation if the hash is captured.
- Encryption uses a key to secure passwords, making it difficult to reverse back to plaintext without the key. Cisco Type 6 passwords, for example, enable secure storage of plaintext passwords on devices, which is particularly useful for VPN keys. Best Practices for Cisco Password Management
Given the vulnerabilities that can arise from improperly protected configuration files, it is vital to adopt the following best practices:
- Use Modern Hashing Algorithms
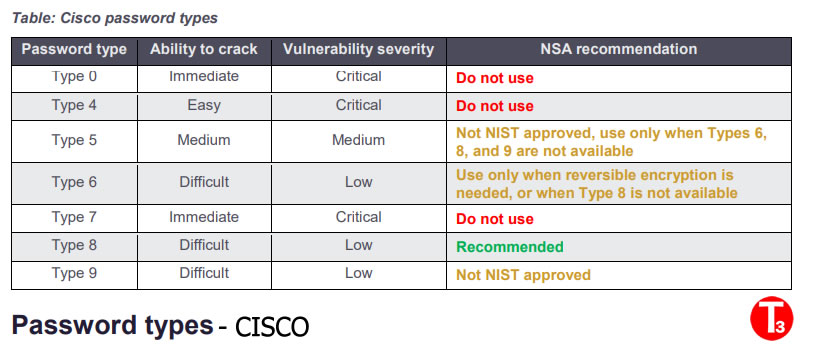
Cisco offers various password protection types, each with varying degrees of security. The following types are recommended:
- Type 8: Utilizes PBKDF2 with SHA-256, making it a secure choice for hashing passwords.
- Type 9: Uses the Scrypt algorithm, designed to resist brute-force attacks by requiring substantial computational resources.
2. Avoid Deprecated and Weak Algorithms
Types 0, 4, 5, and 7 are considered insecure and should not be used:
- Type 0: Stores passwords in plaintext.
- Type 4: Although introduced to reduce brute-force vulnerability, its weak implementation makes it less secure.
- Type 7: Uses a Vigenère cipher with a publicly known key, making it easily reversible.
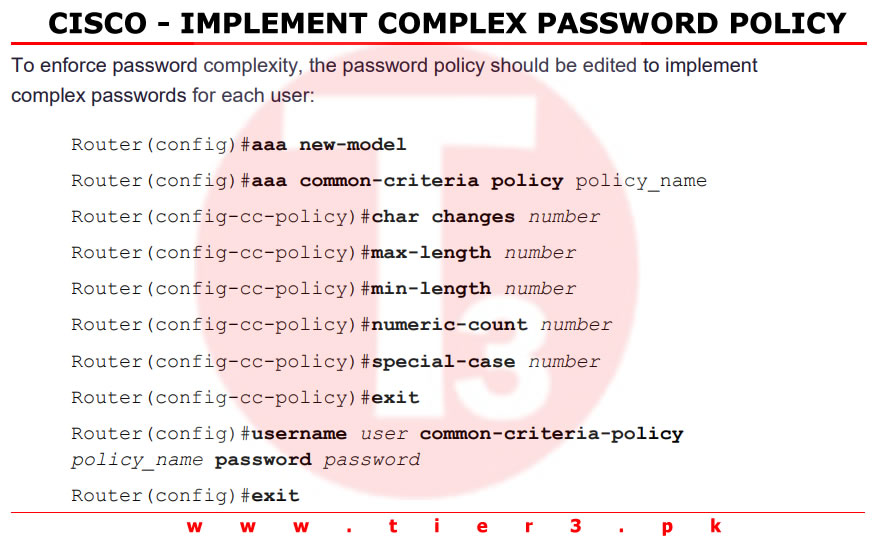
3. Implement Strong Password Policies
To further secure access to privileged EXEC mode, it is crucial to enforce strong password policies:
- Use a mix of uppercase and lowercase letters, symbols, and numbers.
- Ensure passwords are at least 15 characters long and avoid common patterns or easily guessable phrases.
4. Utilize Privilege Levels
In large enterprise networks, Cisco devices offer 16 privilege levels to control command-line access. By customizing these levels, administrators can restrict access to sensitive commands, reducing the risk of unauthorized users compromising network configurations. Conclusion: Securing Pakistan’s Cyber Future
In the context of Pakistan’s growing digital infrastructure, the security of Cisco network devices is paramount. By adopting these best practices, organizations can significantly reduce the risk of network compromise and protect sensitive information from cyber adversaries. As Pakistan continues to develop its cybersecurity capabilities, the implementation of strong, modern password management practices will be a crucial step in safeguarding the nation’s digital assets.





