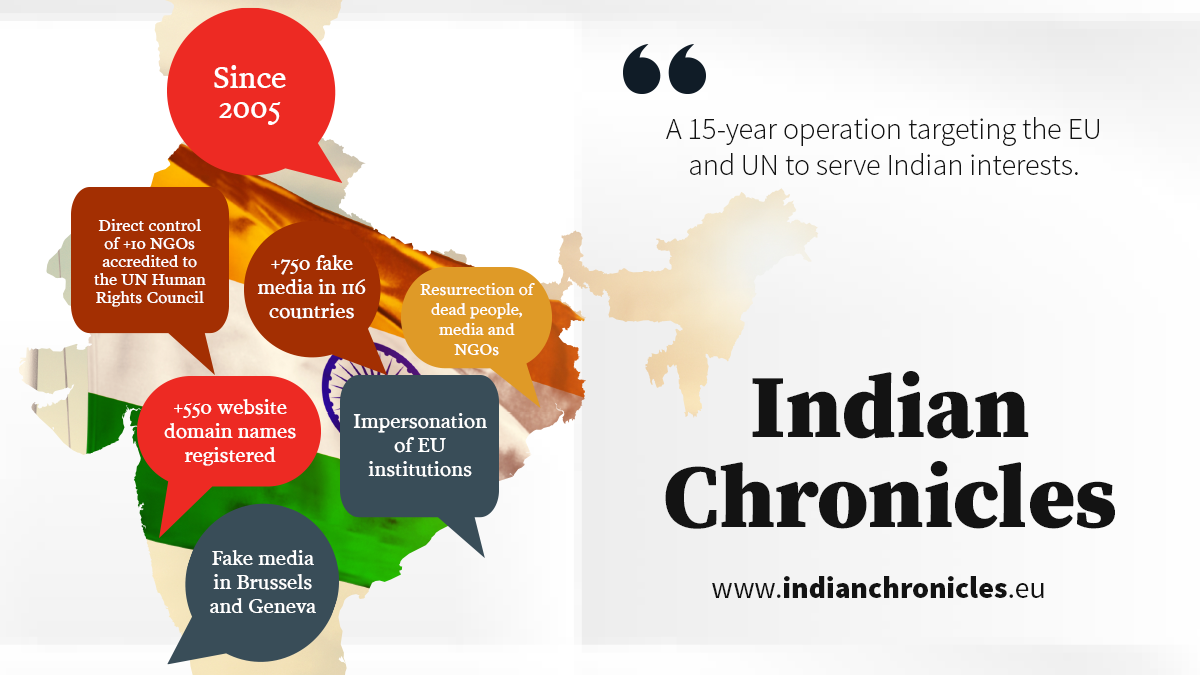
Indian Fake News Mills – State Sponsored Fake News Networks
December 10, 2020
CVE 2018-13379, CVE-2020-12812, and CVE-2019-5591- Exploited to gain access
May 5, 2021There is a known vulnerability and SolarWinds Orion products (affected versions are 2019.4 through 2020.2.1 HF1) are currently being exploited by malicious actors. This attack tactic permits an attacker to gain access to network traffic management systems. There is and Emergency Directive issued By US defence Dept to all federal civilian agencies to review their networks for indicators of compromise and disconnect or power down SolarWinds Orion products immediately.
“The compromise of SolarWinds’ Orion Network Management Products poses unacceptable risks to the security of federal networks,” said CISA Acting Director Brandon Wales. “Tonight’s directive is intended to mitigate potential compromises within federal civilian networks, and we urge all our partners—in the public and private sectors—to assess their exposure to this compromise and to secure their networks against any exploitation.”
Tier3 Threat Intelligence suggests all Pakistani companies operating SolarWinds products should watch out for MITRE ATT&CK framework as possible tactics or attack vector that threat actors are using for persistence in the environment. A similar advisory was released by Fireeye which informs of a highly evasive attack which affected SolarWinds supply chain to Compromise multiple global victims with SUNBURST Backdoor. They have attributed the attack to a previously unknow APT group UNC2452.
It is noted that vendor is aware of these threats and working to provide updated software patches. However, business must wait and remain vigilant on their network activity till these patches are released.





