Cybercriminal Gang Using Google Services for Malware Operations
January 27, 2017Pakistan Cyber Security:Pak Army proposes new network along CPEC
January 29, 2017Experts of the company Proofpoint warn users of Windows and Chrome browser: hackers have come up with a new trick and now disguise their attacks under load additional font package.
The researchers write that attackers rely on a fairly simple technique, they compromise the various sites and add their own production code scripts. These scripts filter incoming traffic, as well as download another malicious script that is dangerous only for Windows-based version of Chrome.
This script, in turn, is responsible for the substitution of HTML-tags on the page to “& # 0”, whereby the content deteriorates and turns into a plurality of character “.” Typically, sites look so if you have problems with fonts and rendering characters.
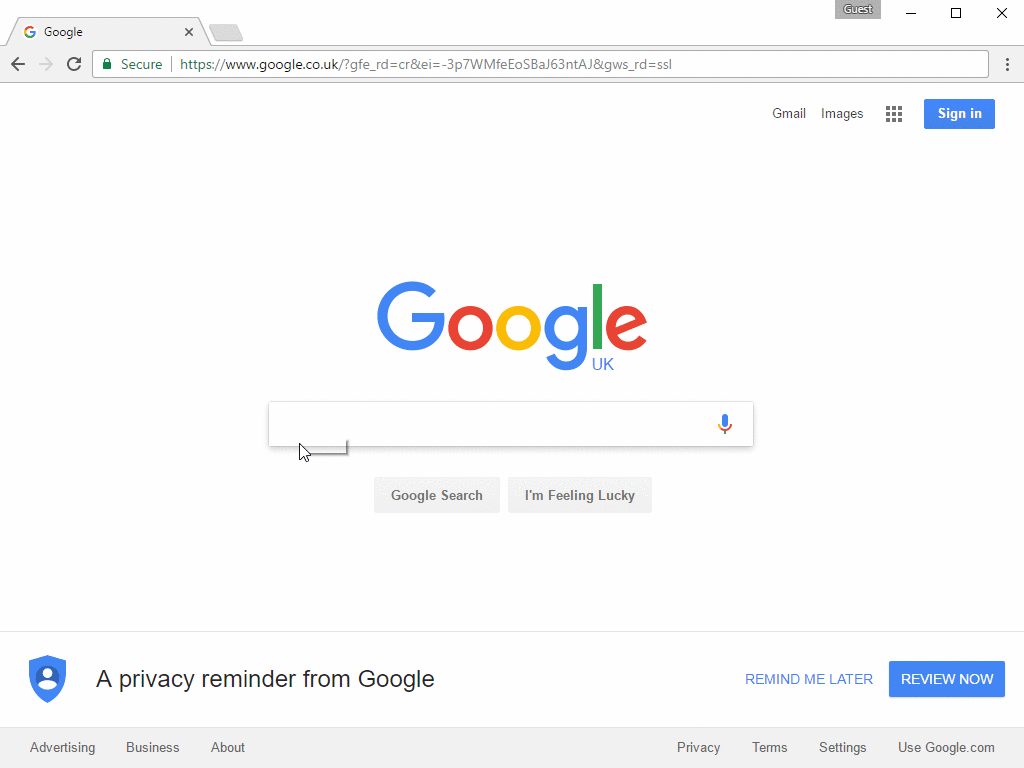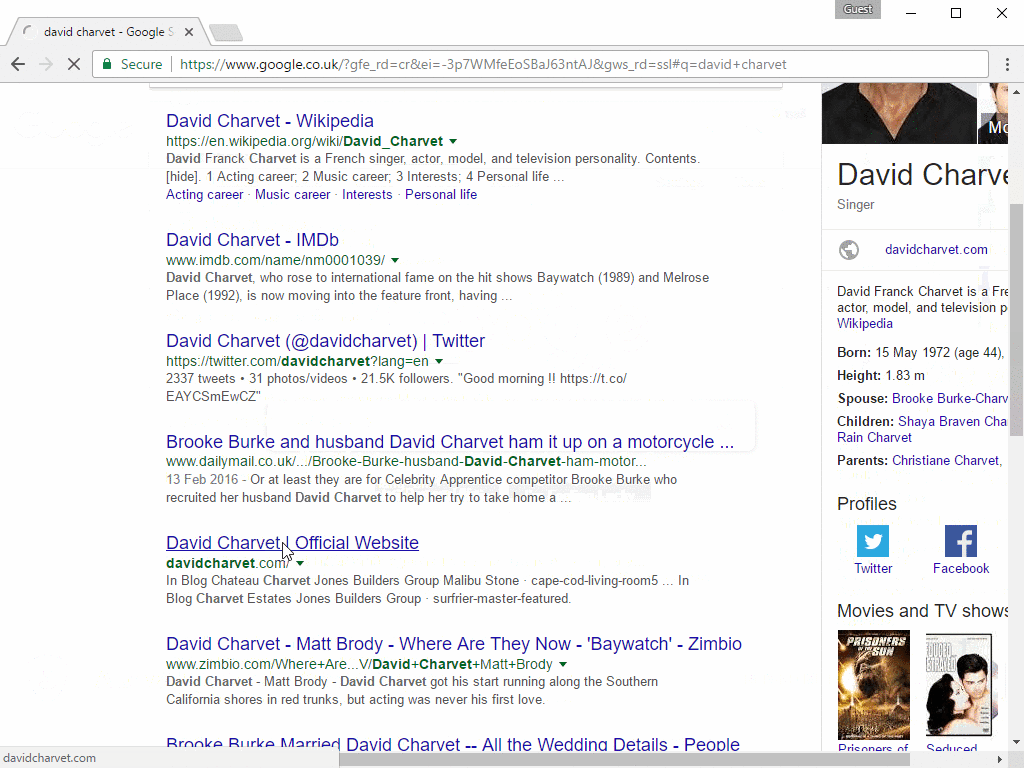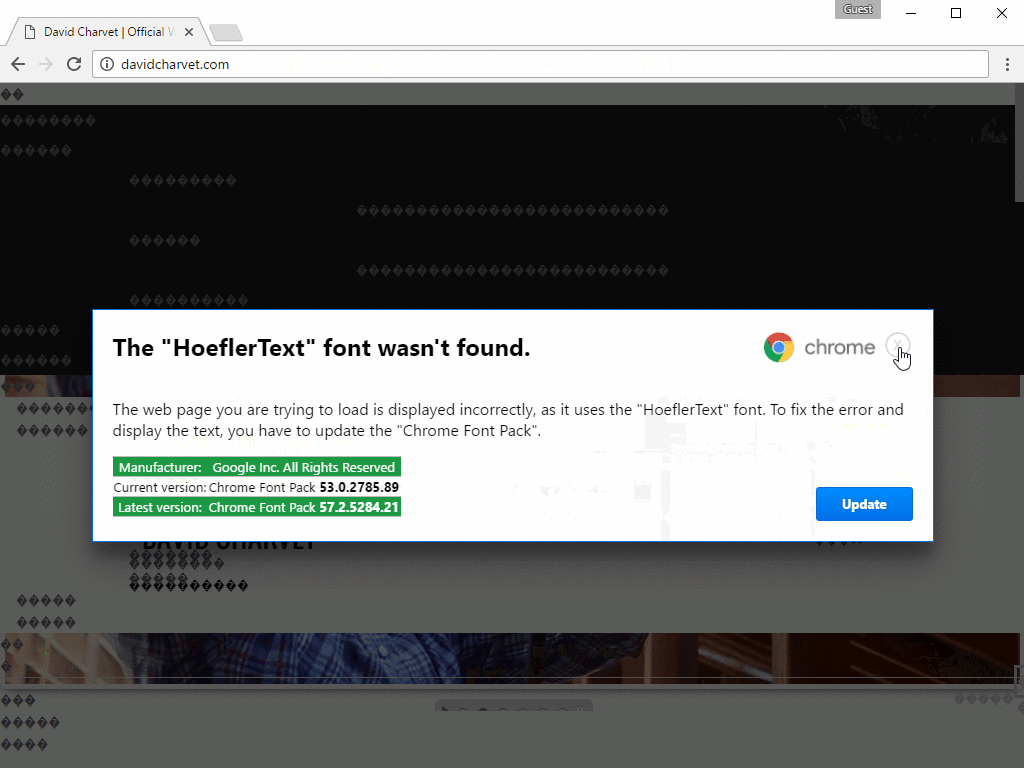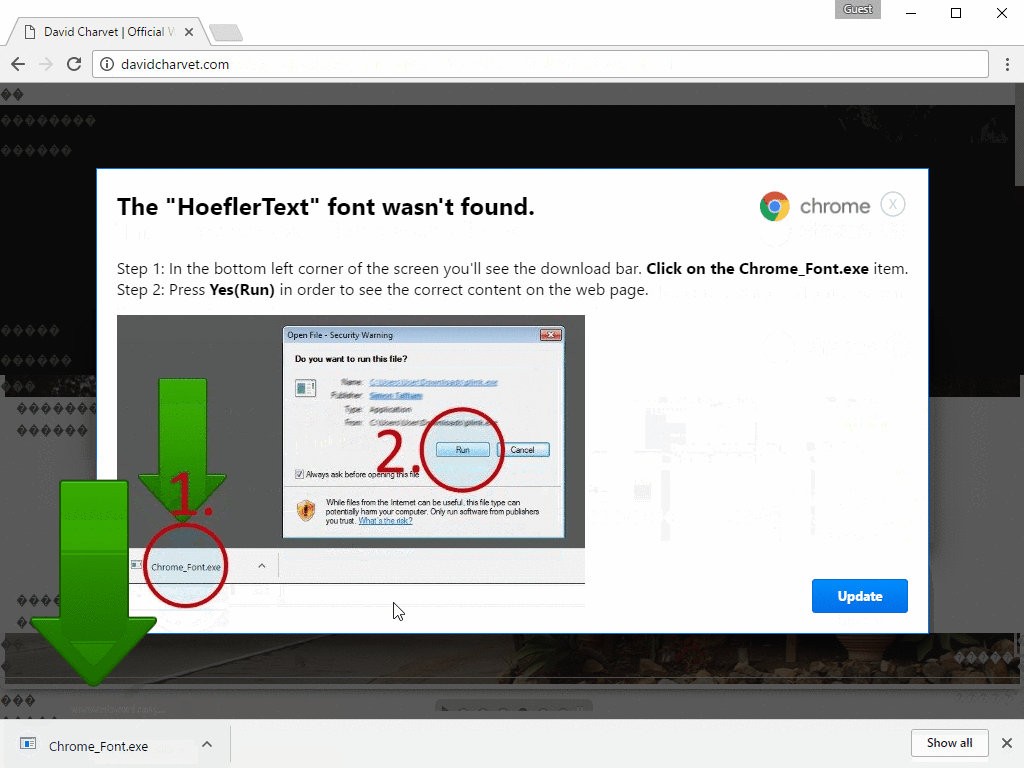
On top of the page, which is becoming unreadable due to the script action, attacking the popup window that informs the victim that her computer does not have enough of a particular font, and for the normal operation of the resource font will need to download and install. Close this window by clicking on the X in the corner, and it will not work. The image below shows all the stages of the attack.
According to our experts, this campaign uses the well-known chain of infections EI Test, first documented as early as 2014. Then EITest strongly associated with the attacks of various exploit kits (for example, Angler and Neutrino), which infected users cryptographers, malware for these abductions and other Malvar. EITest Operators used a simple tactic is very similar to the one described above: they have compromised a large number of sites by exploiting a known vulnerability (mainly victims were resources running WordPress and Joomla control).
Then the attackers redirect a small portion of traffic to infected sites to malicious pages, exposing users to attacks exploit kits and infecting them Malvar.
At the same time the attackers have always acted selectively selecting users that correspond to certain criteria. The new malware campaign is also dangerous only for users from certain countries using Chrome and Windows.
Analysts at Proofpoint, said the technique of “font not found” is strongly related to EITest, despite the fact that in this case, the user must click on the “Update” button (sets exploits with which “collaborated” EITest, as a rule, attacked the victims automatically, without requiring any user interaction).
Experts believe that now the attackers deliberately used elements of social engineering in search of new strategies.
The researchers report that until a new malware campaign distributes a shout-fraud malware Fleercivet.
If you think your system is compromised or you have been affected by this attack please contact Tier3 Cyber security team and we will be able to help you out and clean your system for you.




