
SOLARWINDS ORION NETWORK MANAGEMENT PRODUCTS – Vulnerability
December 14, 2020
IoT (Internet of Things) CyberSecurity Checklist
August 20, 2021APT Actors Exploit Vulnerabilities to Gain Initial Access for Future Attacks.
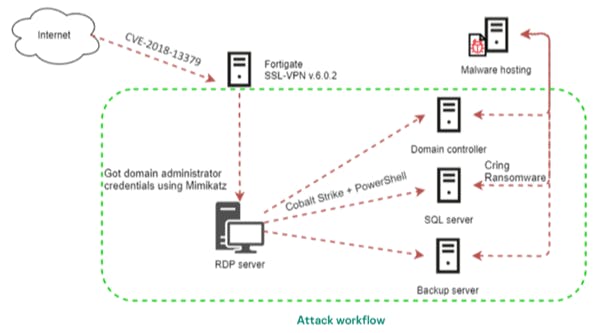
The FBI and CISA have information indicating APT actors are using multiple CVEs to exploit Fortinet FortiOS vulnerabilities. The FBI and CISA believe the APT actors are likely exploiting these Fortinet FortiOS vulnerabilities—CVE 2018-13379, CVE-2020-12812, and CVE-2019-5591—to gain access to multiple government, commercial, and technology services networks.
The APT actors may be using any or all of these CVEs to gain access to networks across multiple critical infrastructure sectors to gain access to key networks as pre-positioning for follow-on data exfiltration or data encryption attacks. APT actors may use other CVEs or common exploitation techniques—such as spear phishing—to gain access to critical infrastructure networks to pre-position for follow-on attacks.
Organizations and businesses in Pakistan should take the following steps for mitigation:
• Immediately patch CVEs 2018-13379, 2020-12812, and 2019-5591.
• If FortiOS is not used by your organization, add key artifact files used by FortiOS to your
organization’s execution deny list. Any attempts to install or run this program and its
associated files should be prevented
Incident response conducted by Kaepersky ICS CERT experts revealed that, in the series of Cring Ransomware attacks, the threat actor exploited the CVE-2018-13379 vulnerability to gain access to the target networks.





