Bypassing Antivirus (AV) and EDR: Techniques, Tools, and Ethical Use
March 6, 2025Once initial access to on-premises infrastructure is established, threat actors will conduct lateral movement to attempt to further expand the scope of access and persistence. To protect Windows endpoints from being accessed using common lateral movement techniques, a Windows Firewall policy can be configured to restrict the scope of communications permitted between endpoints within an environment. A Windows Firewall policy can be enforced locally or centrally as part of a Group Policy Object (GPO) configuration. At a minimum, the common ports and protocols leveraged for lateral movement that should be blocked between workstation-to-workstation and workstations to non-domain controllers and non-file servers include:
- SMB (TCP/445, TCP/135, TCP/139)
- Remote Desktop Protocol (TCP/3389)
- Windows Remote Management (WinRM)/Remote PowerShell (TCP/80, TCP/5985, TCP/5986)
- Windows Management Instrumentation (WMI) (dynamic port range assigned through Distributed Component Object Model (DCOM)) The referenced settings will effectively block all inbound connections for the Private and Public profiles, and for the Domain profile, only allow connections that do not match a predefined block rule.
Computer Configuration > Policies > Windows Settings > Security Settings > Windows Firewall with Advanced Security
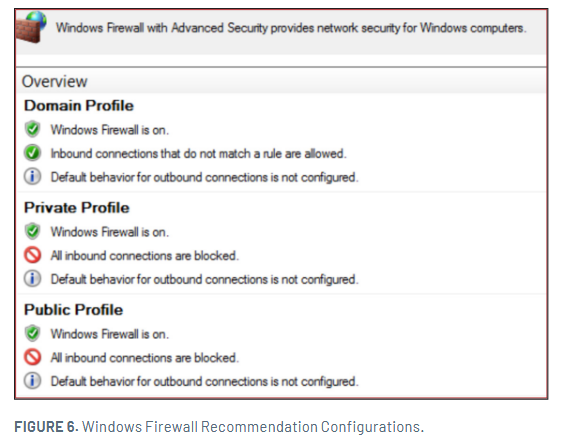
Additionally, to ensure that only centrally managed firewall rules are enforced (and cannot be overridden by a threat actor), the settings for Apply local firewall rules and Apply local connection security rules can be set to No for all profiles.

To quickly contain and isolate systems, the centralized Windows Firewall setting of Block all connections will prevent any inbound connections from being established to a system. This is a setting that can be enforced on workstations and laptops, but will likely impact operations if enforced for servers, although if there is evidence of an active threat actor lateral pivoting within an environment, it may be a necessary step for rapid containment.

Note: If this control is being used temporarily to facilitate containment as part of an active incident, once the incident has been contained and it has been deemed safe to re-establish connectivity amongst systems within an environment, the Inbound Connections setting can be changed back to Allow using a GPO.
If blocking all inbound connectivity for endpoints during a containment event is not practical, or for the Domain profile configurations, at a minimum, the protocols listed in Table should be enforced using either a GPO or via the commands referenced within the table.

For any specific applications that may require inbound connectivity to end-user endpoints, the local firewall policy should be configured with specific IP address exceptions for origination systems that are authorized to initiate inbound connections to such devices.