Hitachi Payment (India) Confirms ATM malware hit
February 13, 2017US visitors must hand over Twitter, Facebook handles by law
February 18, 2017Analysts at Trend Micro reported about a new variant cipher Cerber. This pattern is different from previous versions and other similar Malware unusual feature: it does not touch the antivirus files, firewall and other similar products, not interfering with their work.
The new version, which Trend Micro is held under the classification identifier RANSOM_CERBER.F117AK, was seen more January 20, 2017. Since then, experts are trying to figure out what caused the strange behavior Malware. Typically, the malware trying to bring security solutions fail or prefer them not to communicate and work rolled up, revealing a particular antivirus product on the infected machine. However, the new model Cerber antivirus software and firewalls are registered in the “white list”, ie the extortionist does not encrypt the files of these applications. For these purposes Cerber uses Windows Management Interface (WMI).
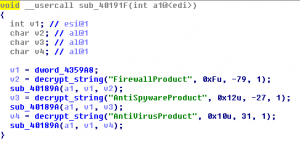
The researchers suggest that security software has got to the exceptions list for the same reasons that were previously in the exceptions EXE- and DLL-files, as well as applications from the Program Files folder.
“I assume that this is due to the fact that antivirus programs do not like it when something changes the files in their own directories. Although most victims Cerber antivirus or not, or installed something not very good “, – said independent researcher MalwareHunter, who also examined the new version of the malware.