
Ransomware Attacks in Pakistan – LockBit 3.0
March 20, 2023
Pakistan on List of States Attacked by GoldenJackal APT
June 7, 2023Malverposting is the practice of distributing malware to a large number of people through promoted social media posts on platforms like Facebook, Twitter and Instagram. During one such campaign, the threat actor distributed information stealer variants such as SYS01 Stealer on social media platforms, infecting over 500,000 devices.
These threat actors hijacked popular social media accounts and also created new business accounts to use in malverposting attacks. These accounts, served sponsored posts that offered free downloads of adult-rated photo albums in ZIP formats, coupons for discounts or other click baits to attract the innocent users.
However, these ZIP files included executable files that trigger an infection chain when opened. The Stealer malware is then downloaded dynamically from C2 servers using curl and 7zip binaries, which are hidden inside the original ZIP payload. These malwares can steal sensitive information, including session cookies and account data.
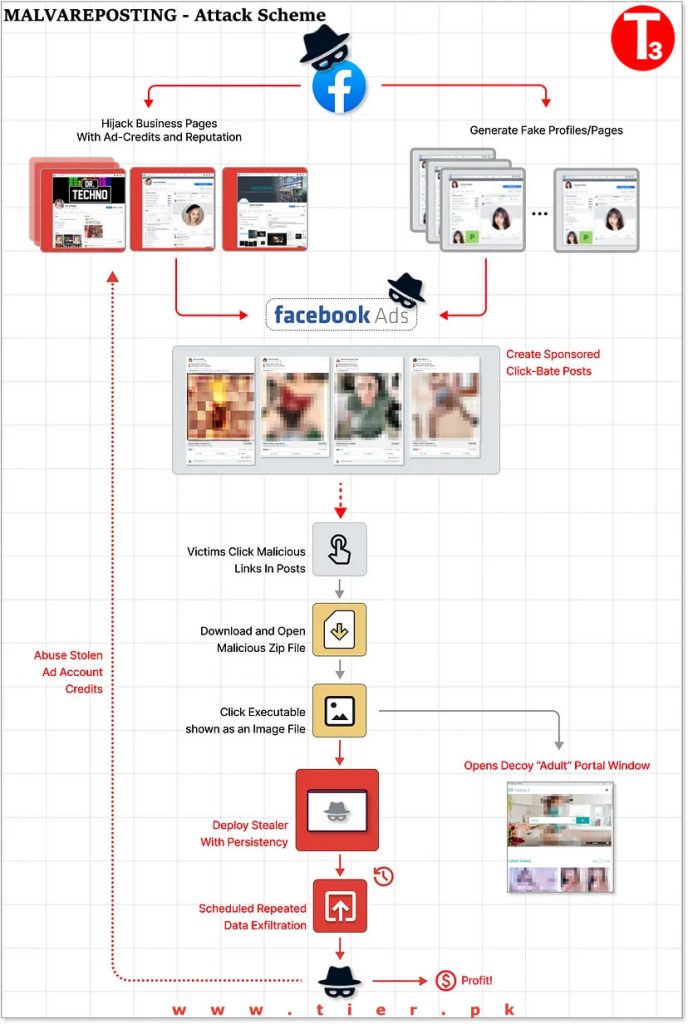
Some of these Facebook accounts targeted by this malverposting campaign belonged to business owners. When their details are compromised, these attacker hijacks their account to leverage the business’s reputation, following their advertisement account (which sometimes still holds funds).
These attacker assumes the identity of the business and branches out to propagate more bad ads through their accounts.
Not only this amplifies the reach, hurting new users, it completely halts the legitimate business activity of reputable brands and stores that may have been building their accounts for years.
What makes some of these attack chains particularly potent is that the attacker uses the stolen data to create additional Facebook bot accounts, used to push more sponsored posts and scale the scheme further. This enables the attackers to distribute millions of copies daily, giving them the time to conduct their malicious activities undetected.
The malicious payload used in the attack is also sophisticated and distinctive, utilizing methods commonly seen in Advanced Persistent Threats (APTs). Looking at the numbers behind these campaigns reveal the scale and efficiency Malverposting can quickly gain. With APIs from Facebook as well as web automation tools — threat actors can automate the entire process and scale it even further.
The newest version of the payload has different variations, all of which begin the infection chain using a seemingly harmless executable file. The attacker used regular system tools associated with well-known Hard-Drive manufacturers such as Seagate and WesternDigital, which could make the attack appear benign and evade detection by antivirus and endpoint security software.
The actual malicious activity is triggered by a sideloaded DLL (also part of the original tool) that was altered to include some obfuscated code to execute the malicious activity once loaded. The original DLL is compiled with .NET technology, and we can see here how decompiling it quickly reveals the added functionality — using assembly and obfuscated strings to further hide itself.
Malverposting campaigns as intense and advance hence are indeed hard to fight back. These malicious payloads are quite sophisticated and vary all the time introducing new evasive techniques. As we’ve seen, it takes time for security vendors to fingerprint it and create relevant verdicts to block — especially when it’s done out of context. And the context is sometimes the major lead, much more than the actual malicious activity.
Since March 2023 alone, we have found around ten malware families using ChatGPT and other similar themes to compromise accounts across the internet. In one case, we’ve seen threat actors create malicious browser extensions available in official web stores that claim to offer ChatGPT-based tools. They would then promote these malicious extensions on social media and through sponsored search results to trick people into downloading malware. In fact, some of these extensions did include working ChatGPT functionality alongside malware, likely to avoid suspicion from official web stores.
When looking at these threats from a wide angle, we see more and more misuse of generally available and legit file hosting, content hosting, and especially delivery mechanisms like Ad-Networks and Social Media. Threat hunting in this endless content stream constantly generated by almost every human in the world is a big challenge, yet seems like one of the most relevant contexts to detect malicious activities.





