Rise of Cybercrime during COVID-19 Pandemic
October 3, 2021
The Wiper Malware
January 1, 2023Fortinet on Monday issued emergency patches for a severe security flaw affecting its FortiOS SSL-VPN product that it said is being actively exploited in the wild.
Tracked as CVE-2022-42475 (CVSS score: 9.3), the critical bug relates to a heap-based buffer overflow vulnerability that could allow an unauthenticated attacker to execute arbitrary code via specially crafted requests.
The company said it’s “aware of an instance where this vulnerability was exploited in the wild,” urging customers to move quickly to apply the updates.
The following fortinet products are impacted by the issue –
- FortiOS version 7.2.0 through 7.2.2
- FortiOS version 7.0.0 through 7.0.8
- FortiOS version 6.4.0 through 6.4.10
- FortiOS version 6.2.0 through 6.2.11
- FortiOS-6K7K version 7.0.0 through 7.0.7
- FortiOS-6K7K version 6.4.0 through 6.4.9
- FortiOS-6K7K version 6.2.0 through 6.2.11
- FortiOS-6K7K version 6.0.0 through 6.0.14
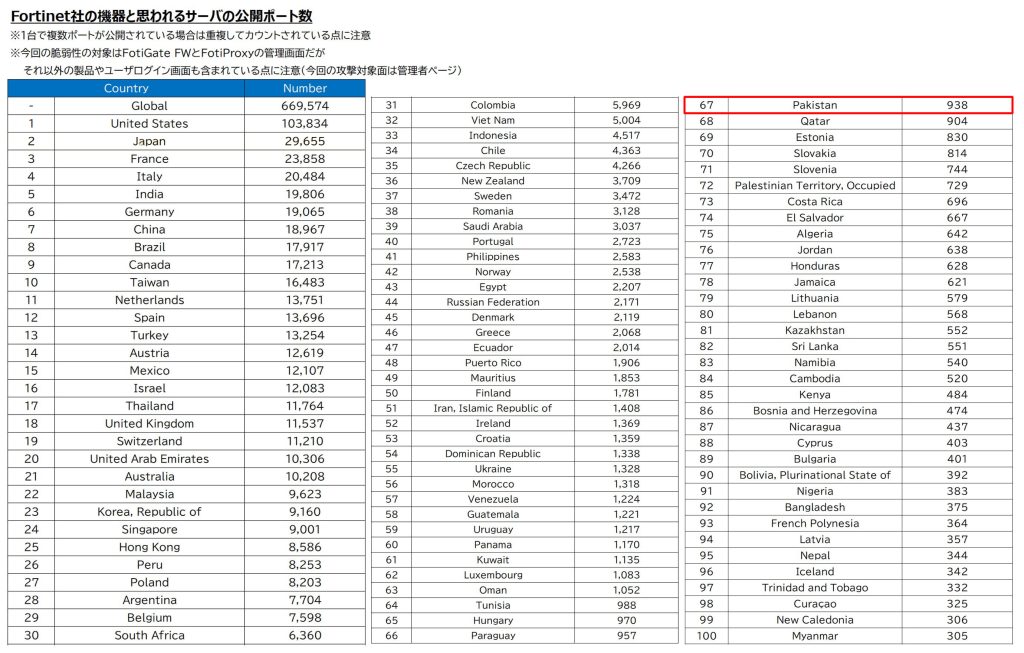
Patches are available in FortiOS versions 7.2.3, 7.0.9, 6.4.11, and 6.2.12 as well as FortiOS-6K7K versions 7.0.8, 6.4.10, 6.2.12, and 6.0.15. A quick scan shows more than 1000 systems affected in Pakistan.