
Security Operations Center (SOC) in Pakistan: What to Log?
August 22, 2024
Common Weakness Enumeration CWE™ – Top 25 Most Dangerous Software Weaknesses list
November 22, 2024Detecting and Mitigating Active Directory Kerberoasting: A Cybersecurity Priority for Pakistani Enterprise Networks
In today’s digital age, cybersecurity has become a top concern for businesses around the world, and Pakistan is no exception. As cyber threats become increasingly sophisticated, one critical area of concern is the compromise of Active Directory (AD) services, including Active Directory Domain Services (AD DS), Active Directory Certificate Services (AD CS), and Active Directory Federation Services (AD FS). These services are fundamental to enterprise IT networks and are often targeted by malicious actors to gain unauthorized access and escalate privileges.
Among the various attack techniques, Kerberoasting has emerged as a significant threat to organizations in Pakistan. Understanding this threat and learning how to detect and mitigate it is crucial for protecting your business from potential breaches.
What is Kerberoasting?
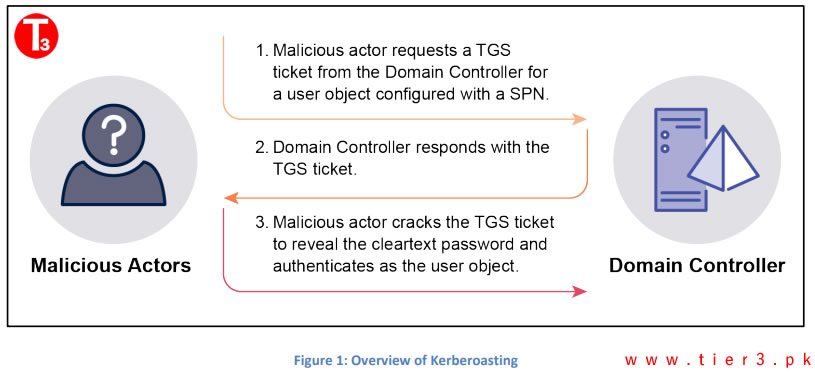
Kerberoasting is a technique that attackers use to exploit service principal names (SPNs) configured for user objects in Active Directory. These SPNs allow any user object to request a Ticket Granting Service (TGS) ticket from a Domain Controller. The TGS ticket is encrypted with the user object’s password hash, which attackers can attempt to crack. Once the password is cracked, they can authenticate as the user, gaining access to sensitive accounts and potentially compromising the entire network.
Service accounts configured with SPNs, particularly those with administrative privileges, are often the target. If these accounts are compromised, attackers can escalate privileges, move laterally through the network, and even gain control of high-level security groups such as Domain Admins, leading to a complete domain compromise.
Why Kerberoasting is a Critical Concern
In Pakistan, where businesses are rapidly digitizing, cyber threats are growing at an alarming rate. Kerberoasting is one of the many techniques used by cybercriminals to exploit weaknesses in Active Directory environments, making it a key concern for IT security teams. As businesses rely more on digital infrastructure, the need for effective cybersecurity measures has never been greater.
Mitigating Kerberoasting
While Kerberoasting takes advantage of normal Active Directory functionality, several security controls can be implemented to reduce the risk:
- Minimize SPN-Configured User Objects: Reducing the number of user objects configured with SPNs limits the attack surface, making it harder for attackers to find vulnerable accounts.
- Use Group Managed Service Accounts (gMSAs): Configuring SPNs as gMSAs can significantly improve security. gMSAs use automatic password rotation, long, complex passwords (120 characters), and simplified SPN management, making password cracking extremely difficult.
- Set Strong Password Policies: If gMSAs cannot be used, ensure that SPN-configured user objects have a minimum 30-character password that is unique and unpredictable to reduce the risk of cracking.
- Limit Privileges: Assign only the necessary privileges to user objects with SPNs, and ensure they are not part of highly privileged groups such as Domain Admins. This reduces the impact in case of a successful Kerberoasting attack.
Detecting Kerberoasting Activity
Detecting Kerberoasting is challenging, as it mirrors legitimate Active Directory activity. However, specific event logs can help identify potential attacks:
- Event ID 4769: Generated when a TGS ticket is requested. Monitoring for multiple requests for SPN-configured accounts in a short time can indicate Kerberoasting activity.
- Event ID 4738, 5136: Generated when user accounts are modified. Attackers often modify user objects to retrieve Kerberos tickets and then remove the SPN after the attack.
By analyzing these events, organizations can detect Kerberoasting attempts and take immediate action to protect their networks.
Conclusion: Strengthening Cybersecurity in Pakistan
With the rise of cyber threats in Pakistan, it is crucial for businesses to adopt robust security measures to safeguard their networks. Kerberoasting is just one of the many techniques used by attackers, and understanding how to detect and mitigate it can help prevent severe damage to your organization.
Protecting your Active Directory infrastructure is not just a best practice—it is a necessity in today’s digital landscape. By implementing the right security controls, monitoring suspicious activity, and staying vigilant, businesses in Pakistan can stay ahead of cyber threats and protect their valuable data from compromise.





