At Tier3 we understand that your business or personal privacy and cyber security is not a matter of some tips and experts opinion. You take it seriously, we take it seriously.
Our experts are always there to provide consultation and best solution to your most private cyber security problems.Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These cyber attacks are usually aimed at assessing, changing, or destroying sensitive information; extorting money from users; or interrupting normal business processes.
Tier 3 cybersecurity consultants, partner with your company and provide the following services: Penetration testing, Attack surface analysis, vulnerability management, website Security and protection, cyber security risk management, Cyber security Policy Development, Cyber security Threat Assessments, and Cyber security Awareness and Training programs.
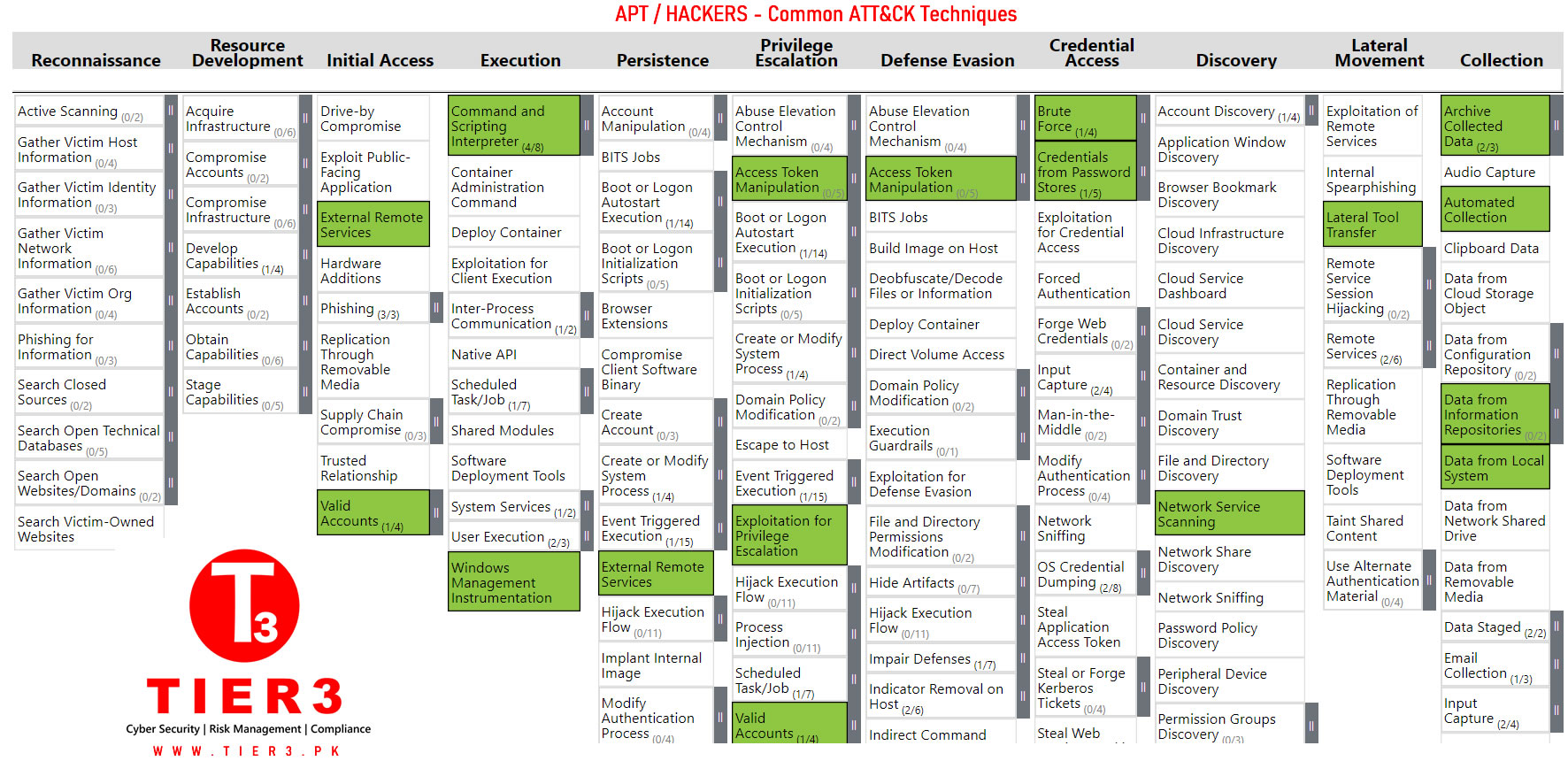
APT / Hackers - Common ATT&CK Techniques
Our Cyber security operations services include firewall, IDS/IPS, incident management, and incident response. When operating and maintaining a network or system, experience is paramount. Our niche experience in managing highly secure environments of major enterprises has proven that, by closely integrating security and operations, the cybersecurity of the network dramatically increases.
Consulting with experienced cyber security professionals at Tier3 provides unparalleled peace of mind. Vulnerabilities can be identified and risks appropriately prioritized. Your security stance can be greatly improved. Your team can even be taught how to maintain your improved security configuration going forward.Tier3 provides consultation to build a Zero Trust Network . We operate with in a cyber defence strategy of Cybersecurity mesh - a strategy that independently secures each device with its own perimeter — such as firewalls and network protection tools. Creating a cybersecurity mesh requires new endpoint and user-focused solutions that keep each individual device secure.
Our cyber defence security framework dictates that organizations should not trust any entity inside or outside of their perimeter at any time. It provides the visibility and IT controls needed to secure, manage and monitor every device, user, app and network being used to access business data.
Tier3 can help your organization by adopting many different solutions to individually secure each device and endpoint in environment, including:
- Multi-factor authentication to verify user identity
- Disc and data encryption to secure all company information
- Remote wipe tools in case an endpoint is lost or stolen
- Virtual private networks to safeguard communications
- Limited remote access gateways that enforce least privilege user access
- Modern monitoring and correlation tools for threat detection
Experiencing a cybersecurity attack?
Services for Individuals :
Read more about online and cyber blackmail in Pakistan and its examples.
Implementing effective cybersecurity measures is particularly challenging today because there are more devices than people, and attackers are becoming more innovative. If you believe your whatsapp account hacked you can read and follow our easy guide to recover your whatsapp account back in Pakistan.
Anti-Virus & Ransomware Removal Solutions
To purchase anti virus and anti malware software for cybersecurity Pakistan for your personal or business needs please visit here.
Please email info(@)tier3.pk for more information.

