Static application security testing (SAST), or static analysis, is a testing methodology that analyzes source code to find security vulnerabilities that make your organization’s applications susceptible to attack. SAST scans an application before the code is compiled. It’s also known as white box testing.
Getting the most out of SAST starts with the realization that dev and sec teams have different—but complementary—needs.
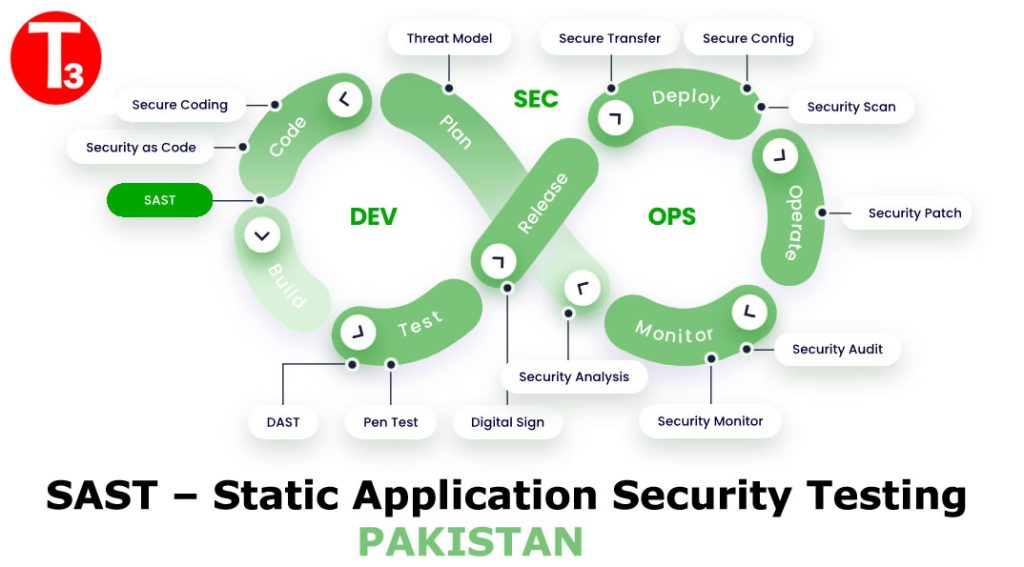
Why does your team need SAST?
With application-level attacks on the rise and delivery schedules only getting shorter, it’s important to have SAST’s insights on potential vulnerabilities in newly written code early and often in the development process. SAST can also be run on older code so security debt can be prioritized and addressed.
SAST, DAST, IAST, and RASP
A number of tools exist to test or protect applications throughout the software development lifecycle (SDLC). SAST, DAST, IAST, and RASP are sometimes confused with one another. We’ll briefly go over them here and in the next section we’ll go deeper into the differences between SAST and DAST.
- Static Application Security Testing (SAST) looks for weaknesses in custom code at rest
- Dynamic Application Security Testing (DAST) performs automated attacks on applications to test them for weaknesses when they are running
- Interactive Application Security Testing (IAST) combines DAST capabilities with SAST insights
- Runtime Application Self-Protection (RASP) is built into a program to protect it after deployment. It is capable of detecting and preventing external threats in real time.
SAST tool for your organization in Pakistan
The application security market is full of SAST offerings, often bundled up with additional solutions, making it a challenge to find the right fit for your organization.
OWASP’s list of criteria for selecting the right SAST tools can help companies narrow down the options and choose the solution that best helps them improve their application security strategies.
- Language support. Make sure the SAST tool that you use offers you complete coverage for the programming languages your organization uses.
- Vulnerabilities coverage. Make sure that your SAST tool covers at least all of OWASP’s Top Ten web application security vulnerabilities.
- Accuracy. Your SAST solution should be capable of minimizing the false positives and false negatives that create unnecessary work. So, it’s important to check the accuracy of the SAST tools that your organization is considering.
- Compatibility. Like any automated tool, it’s important that the SAST tool you use is supported by the frameworks you are already using so that it integrates easily into your SDLC.
- IDE integration. A SAST tool that can be integrated into your IDE will save you valuable remediation resources.
- Easy integration. Find the SAST tool that is easy to set up and integrates as seamlessly as possible with the rest of the tools in your DevOps pipeline.
- Scalability. Make sure the SAST tool you integrate today can be scaled to support more developers and projects tomorrow. A SAST tool can seem to scan quickly on a small sample project; make sure it delivers similar results on larger projects.
Identify potential security vulnerabilities and coding errors by implementing Software supply chain security. Looking for more details about our solutions ? – Start building a proactive AppSec program today – Talk to us

