
Cyber Security Course in Pakistan
! Imp Note
- Unlike others we do not teach many things. We only Know, Practice and Teach Cybersecurity.
Visit Our Cybersecurity Training Portal
Whether you are new to cyber security or a seasoned cyber security practitioner, ethical hacker or bug bounty hunter with a specialized focus, Tier3 cyber security training and cyber security course in Pakistan provides the essential knowledge, hands on cyber security training, information security skills and techniques you need to protect and secure critical information and technology assets, whether on-premise or in the cloud. Learn to be among the Top Hackers in Pakistan.
Tier3 shows you how to directly apply the concept learned into a winning defensive or offensive strategy on our cyber range and virtual practical cyber security labs, all in the terms of the modern adversary.The aim of our course outline for cyber security and training is to show you how to emulate a potential adversary cyber attack in complex environments, cyber threat intelligence, Red Team or Blue team tradecraft, and engagement planning. Explore by going beyond penetration testing, you will learn to conduct successful Red Team engagements and challenge the defence capability.
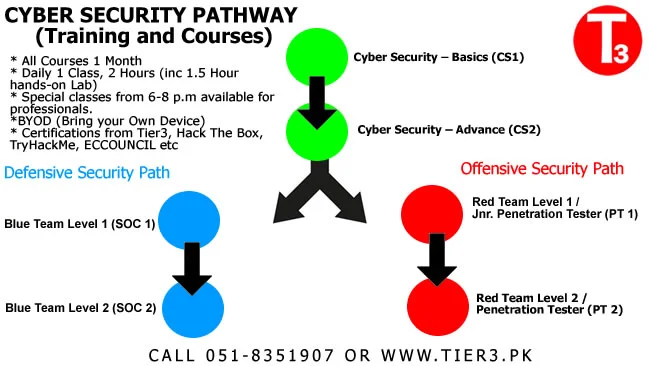
* Cyber Security course duration in Pakistan is 1 Month.
* Cyber Security course fees in Pakistan is starting from 35,000 Rs
* Are there any online cyber security training courses available in specifically for Online Pakistani Learners in local language ? - Yes, our cyber security online courses starts from 25,000 Rs for 1 Yr access to the course content and supporting labs.
Want to Learn Remotely at your Own Pace?
Check Out Our Online Cyber security Courses
Visit Our Youtube channel to view online cyber security courses introductions and session recordings.
Our Online Lectures / Classes and Labs explanatory videos use Urdu as primary language for teaching.
Our course content, lectures and the other supporting teaching materials are developed specially, keeping the Pakistani cyber security learners in mind.
You can contact our customer services to ask more about the prices of complete online cyber security courses in Pakistan and their availability.
Please note - Not all courses are available for online studies. Extra oncall/virtual 1-1 tutoring can be added as addon.
*Online cyber security course pack includes all of the relevant course material and local or remote test / Lab (Cyber Range) environment access where required.
Get in touch with our team if you want to know more about cyber security course schedule and costs or Diploma in Cyber security in Pakistan online fees.
Cyber security course
- Cybersecurity fundamentals
- Basic concepts of Cyber Security.
- Learning cyber security for beginners
- Key cybersecurity practices
- Identify various types of malicious software.
- Best cyber security course in Pakistan for beginners
- Threat actors and APT attacks
- Ethical hacking, bug bounty hunting, OSINT
- Introduction to C2 infrastructure
- Hands-on labs in a virtual environment
- Identify key cybersecurity tools e.g firewall, anti-virus, cryptography, penetration testing and digital forensics.
- Network security controls and Secure architecture
- Cloud security issues and terminology
- and More ...
Offensive Security Course
- Learn from Top Hackers in Pakistan.
- Setting up an environment , Red Team Exercises and Adversary Emulation
- Properly plan and prepare for an enterprise penetration test
- Establish resilient, advanced C2 infrastructure
- Execute extensive post-exploitation to move further into the network with persistence
- Attackers techniques to evade endpoint detection tools
- Ethical hacking and bug bounty hunting
- Nmap and NSE, ARP scan and network discovery,Google dorks & Shodan
- Hacking Wi-Fi networks / WPA2 / ARP, HTTPS / DNS and DHCP
- Hacking routers and VPN Networks, Cloud & Network Penetration, windows systems, Exploiting Domains and AD
- Hash Algorithm Attacks, IoT Hacking and Pivoting Attacks
- and More ...
Cyber Defense Course
- Blue Team Exercises and Adversary Emulation
- Defend against the attacks specified in OWASP Top 10
- Blue Team Fundamentals - Attack surface Analysis and Cyber threat intelligence, Active Cyber defense, access control & password management
- Protect cloud-hosted workloads, services, and virtual machines
- Identify and comprehend deficiencies in security solutions
- Reverse Engineering Malware and Traffic analysis
- Web communication security, virtualization, API security, and endpoint security
- Advanced cryptography (hashes, digital signature, encryption) and Full disk encryption
- Anonymity and Privacy - Dark Web, Open-Source Intelligence (OSINT)
- Vulnerability Assessment Systems - OpenVAS
- and More ...
Cyber security Course in Pakistan- Training & Certifications
Burp Suite Certified Practitioner
Metasploit Pro Certified Specialist
Penetration Testing with Kali Linux
Cyber Threat Intelligence
Exploit Development
Reverse Engineering with IDA Pro
Network Forensics & Incident Response
Smartphone Forensic Analysis
Certified Ethical Hacker C|EH® v12
Computer Hacking Forensic Investigator - CHFI v10
PEN-200: OSCP Certification
IACS Cybersecurity Design & Implementation (IC34M)
Laptop Requirements : A properly configured system is required to fully participate in these courses. Important! Bring your own system configured according to these instructions. Back up your system. Better yet, use a system without any sensitive/critical data. Tier3 is not responsible for your system or data. MANDATORY HARDWARE REQUIREMENTS 1.CPU: 64-bit Intel i5/i7 (8th generation or newer), or AMD equivalent. A x64 bit, 2.0+ GHz or newer processor is mandatory for this class. 2.CRITICAL: Apple systems using the M1/M2/M3 processor line cannot perform the necessary virtualization functionality and therefore cannot in any way be used for this course. 3.** BIOS settings must be set to enable virtualization technology, such as "Intel-VTx" or "AMD-V" extensions. Be absolutely certain you can access your BIOS if it is password protected, in case changes are necessary. 4.* Wireless networking (802.11 standard) is required. There is no wired Internet access in the classroom or Labs.
Cyber Security Course Fees in Pakistan
Overall, the fees structure of a cyber security course and cyber security bootcamp in Pakistan depends on various factors, including its duration, technical level, resources / labs required to complete the course, and additional facilities/resources provided. It's essential for prospective students to consider these factors when evaluating the cost-effectiveness and value of a course. Most of the basic courses start from 35,000 Rs/month and prices increase or varry considering aforementioned factors.
Best Cyber Security Course in Pakistan
| 👍Best for: | Individuals, Students, Cybersecurity enthusiast, Corporates, Govt, Financial Institutes |
| ₨ Fees: | 35,000 Rs onwards (Depending on course) |
 ✅ Courses: ✅ Courses: | Basic cyber security, Offensive Cyber Security, Cyber Defence, Malware analysis, Ethical Hacking, Threat Intelligence etc |
| ✓ Speciality: | Accelerated cyber security training program. Professional cyber security course in Pakistan |
| ✍️ Improves: | Advanced Red, Blue and Purple team techniques and training |
| 🔥 Types: | Cyber threat intelligence, Red Team or Blue team tradecraft, and engagement planning |
| 🌐 Training: | Advanced technical training, industry-recognized cyber security certifications, and hands-on cyber defense and incident handling and foundational cyber skills |
| 💡 Availability: | Pakistan (All cities) |
| ⌛ Time: | 3 Days, 7 Days, 1 month and 3 Months |
We collaborate with a broad community of cyber security professionals and organizations in Pakistan. We share and pursue our mission and commitment to create a diverse, capable, and innovative cybersecurity industry in Pakistan.
- Cyber Workforce Academy
An accelerated cyber security training program that provides job seekers and novice ethical hackers with advanced technical training, industry-recognized cyber security certifications, and hands-on cyber defense and incident handling skills sought by local employers in Pakistan.We leverage our expertise and our cybersecurity training capabilities to deliver research, cyber toolkits, cyber ranges, and many other widely available learning opportunities for individuals and organisations.We teach you principles of cybersecurity that will last for years, using a hands-on approach, but not neglecting theory, which is the basis of deep understanding. Our training will help you adopt the “shifting left” mindset where security issues are addressed early and quickly. - Red Team ToolKit
Red Team Toolkit is an offensive security platform and tooling suite used and recommended by our Tier3 Penetration testers. It optimizes the red team operations and penetration tests. This toolkit enables penetration testers to perform advanced network operations, collaborate on target exploitation, and better simulate sophisticated adversaries.Our Red Team Toolkit drives stealthy cyber security operations through all phases of an attack, including reconnaissance, initial access, privilege escalation, persistence, and impact. It includes more than 50 regularly updated Tools and source code review tools. Each tool has a specific purpose to facilitate stealthy operations and adversary emulation.
Cyber Security Course in Pakistan
The Tier3 cyber security Training scheme and cyber security courses provides a benchmark for cyber security training and education in Pakistan by assuring the quality of both content and its delivery.
The demand for cybersecurity talent is high and critical roles go unfilled each year due to a years-long talent shortage in Pakistan. If you are looking for a career that offers lots of opportunities for learning, rewarding work, and zero stagnation, consider cyber security.
Our cyber security course in Pakistan is designed to strengthen your technical skillsets. This course will help system administrators, defenders, and others in security to understand the mindset and methodology of a modern attacker. Every organization needs skilled cyber security personnel who can find vulnerabilities and mitigate their effects. The entire course is specially designed to get you ready for that role. Remember both the offensive teams or defenders have the same goal: keep the bad guys out.
Find out more on how Tier3 can help you to get into cybersecurity with little to no technical experience, information on the types of roles and courses we offer with-in cybersecurity domain and resources to help you learn more about this exciting, in-demand field.
We add new content often so make sure to visit us regularly. If you have any questions about getting into cyber security course in Pakistan, or want to find out more about fees or admissions contact us or follow us on twitter to stay updated.

